Ask any security professional and they’ll tell you that remediating risks from various siloed security scanning tools requires a tedious and labor-intensive series of steps focused on deduplication, prioritization, and routing of issues to an appropriate “fixer” somewhere in the organization. This burden on already resource-strapped security teams is an efficiency killer.
A new study, commissioned by Seemplicity and conducted by Dark Reading, provides fresh insight into how security pros handle the challenging remediation life cycle from discovery to resolution. The research reveals the obstacles security professionals face when coordinating remediation activities. The data exposes the outcomes — in increased workload and diminished risk posture — that arise from lengthy remediation times, inefficient and uncontrolled manual processes, the lack of managerial visibility and oversight across the risk life cycle.
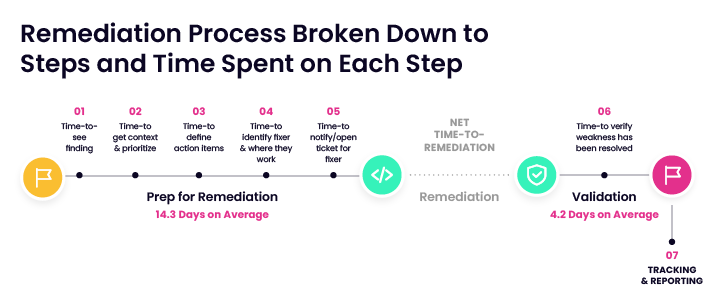 |
| Remediation Process Broken Down to Steps and Time Spent on Each Step |
The survey, which encompassed 108 cybersecurity professionals, at companies with 100 or more employees, found that:
- It takes nearly 4 weeks to remediate critical security risks from start to finish. A granular look at the end-to-end risk- reduction process shows remediation life cycles consistently measured in weeks, not days.
- The average organization manages 3 to 5 security tools, adding complexity and slowing down remediation. The data clarifies that manual tasks and multiple feeds from disparate scanning tools conspire to drag down speed-to-remediation.
- 49% of security professionals don’t know who to contact to fix risks or verify fixes. Locating the correct fixer, getting a response to a remediation request, and verifying successful fixes are top-time consumers for most organizations.
- 97% would focus on proactive security tasks if remediation was efficient. Were there better and faster ways to remediate risks, respondents said they would spend the time gained on forward-looking activities, such as additional architecture review, threat modeling, and security awareness training.

If there’s one recurring theme in the research, it’s that the combination of too many security tools and too much manual work being conducted across different teams blocks efforts to keep pace with today’s risk reduction and remediation workloads for the majority of organizations.
The “State of Risk Remediation” research provides a roadmap for improving efficiency and performance, bolstering organizational defense, and reducing risk — and security team’s sanity.
The report also highlights three key steps to improving risk reduction:
- Automating risk reduction workflows will allow security teams to focus on strategic security initiatives. Employing judicious automation technology at every point in the remediation process and across disparate scanning and management platforms frees teams to focus on more strategic security initiatives while also improving remediation efficiency and performance.
- Acknowledging remediation has many moving parts will contribute to more effective remediation. Effective prioritization, along with the ability to aggregate congruent issues in a single remediation ticket, are key steps in making risk remediation manageable.
- Risk reduction workflows require specific security knowledge. An automated remediation workflow tasked with organizational risk reduction is only as good as the security expertise it’s built on.
Download the full research report “The State of Risk Reduction: A Need for Speed” here.
