SaaS applications are the backbone of modern businesses, constituting a staggering 70% of total software usage. Applications like Box, Google Workplace, and Microsoft 365 are integral to daily operations. This widespread adoption has transformed them into potential breeding grounds for cyber threats. Each SaaS application presents unique security challenges, and the landscape constantly evolves as vendors enhance their security features. Moreover, the dynamic nature of user governance, including onboarding, deprovisioning, and role adjustments, further complicates the security equation.
With great convenience comes great responsibility, as securing these SaaS applications has become a top priority for Chief Information Security Officers (CISOs) and IT teams worldwide.
Effectively securing SaaS applications requires a delicate balance between robust security measures and enabling users to perform their tasks efficiently. To navigate this complex terrain, this article excerpts a step-by-step guide to establish a robust SaaS security strategy – from planning to execution and performance measurement.
Map Your Apps and Security Requirements
Before embarking on a SaaS security journey, it’s imperative to understand your organization’s specific landscape and security needs. While applications like Salesforce and Microsoft 365 may contain more critical data, even smaller, niche apps used by various teams can store sensitive information that must be protected.
Consider the regulatory and compliance requirements applicable to your business. Industries such as finance adhere to SOX, while healthcare organizations must comply with HIPAA. Understanding your regulatory environment is essential for shaping your security strategy.
Additionally, prioritize user access and data privacy. Implementing the principle of least privilege (POLP) ensures users have access only to the data required for their roles, reducing the risk of data breaches and unauthorized access. If your apps handle personally identifiable information (PII), ensure your security program aligns with privacy laws.
Here is some basic info you should collect for each app:
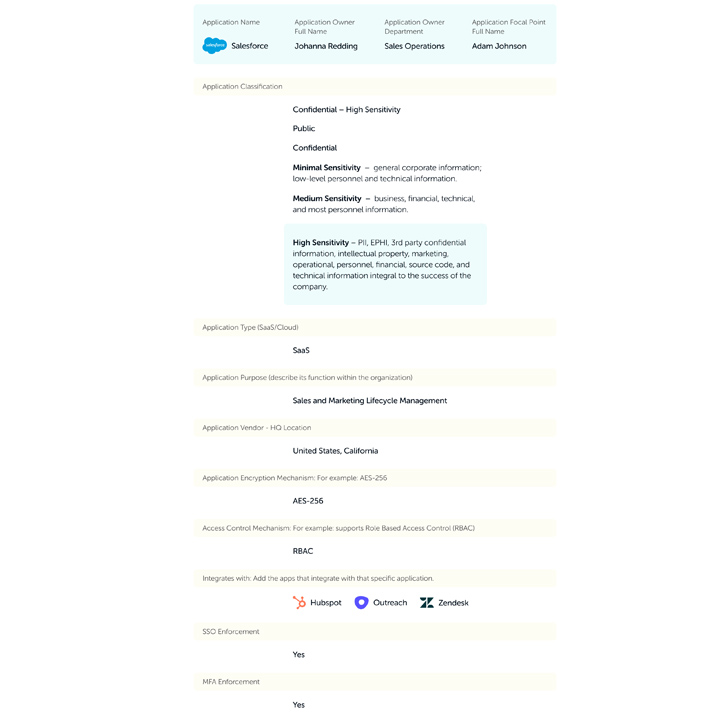
To read the full Kickstarting Your SaaS Security Program guide, click here.
Map Your Existing Security Ecosystem and How You Plan to Integrate SaaS Security Tools and Processes
To be most effective, your SaaS security program must integrate tightly into the existing infrastructure. It must connect with the organization’s Identity Provider (IdP) for effective user governance and your single sign-on (SSO) provider to make it more difficult for unauthorized users to access the SaaS stack. These integrations enhance the protection of your applications and make it easier for security professionals to do their job.
It’s also important to integrate your SaaS security tools with existing SOC, SIEM, and SOAR tools. The SOC team can analyze alerts and quickly make a determination as to the mitigation required. Meanwhile, SIEM can manage events while SOAR can orchestrate remediations, deprovision users, and automate many of the mitigations needed to secure the SaaS stack.
Identify Stakeholders and Define Responsibilities
SaaS security is a collaborative effort involving multiple stakeholders. Business units manage SaaS applications with a focus on productivity, while the security team’s priority is data protection. Bridging the gap between these groups and deciphering the unique language of each SaaS application’s settings is challenging.
Effective SaaS security demands collaboration and compromise between these parties to mitigate risks without hindering productivity.
Define Short-Term and Long-Term Goals
Creating a successful SaaS security program requires clear goals and key performance indicators (KPIs) to measure progress. Begin with a pilot program focused on critical applications managed by different departments. Establish a timeline for the pilot, typically around three months, and set realistic improvement goals.
A posture score, measured on a scale of 0-100%, can help gauge security effectiveness. Aim to maintain a score above 80% at the conclusion of a three-month pilot program and target a long-term score of 90-100%.
Increase Your Initial Security Posture
Start by securing high-risk, low-touch items in collaboration with app owners. Close communication is crucial to understanding the impact of security changes on workflows and processes. Address high-risk security checks impacting a small number of employees first. Utilize Security Posture Management solutions to guide remediation efforts based on application, security domain, or severity.
Some organizations choose to improve posture one application at a time. Others improve posture by domain across multiple applications, while still others choose to remediate issues by severity regardless of the application. Whichever model you choose, it is important to develop a process to help you move systematically through your applications.
Schedule Ongoing Check-In Meetings to Maintain and Keep Enhancing Your Posture
Frequent meetings with stakeholders involved in remediation are essential, especially during the pilot phase. As the posture stabilizes, adjust the frequency of these meetings to ensure sustained security.
Continue onboarding and monitoring additional applications to enhance the security posture of your entire SaaS stack.
Adopt a Strict Identity & Access Governance Policy
Embrace the principle of least privilege (POLP) to restrict user access to essential tools and data. Deprovision users who no longer require access to minimize risks associated with active accounts. Regularly monitor external users, particularly those with admin rights, to safeguard app data.
By adhering to these principles and following a structured approach, organizations can establish a robust SaaS security program. Remember, SaaS security is an ongoing process, and continuous adaptation and improvement are key to staying ahead of evolving threats in the digital landscape.
Learn how to streamline and automate securing your SaaS stack.
